With the advent of the intelligent era of the Internet of Things(IOT), smart home solutions from mainstream brands such as Apple HomeKit, Xiaomi Mijia, Haier U-Home are also shifting people’s lives. As housing and transportation become more and more convenient, personal data security is also facing more and more challenges. This article mainly takes Xiaomi's smart home solution as an example to discuss the smart home forensics method and the data sources that can be extracted.
The operation mode of the Mijia smart home solution: Peripheral surveillance cameras, human sensors, smart switches and other sensor devices are connected to the smart gateway through ZigBee to achieve data collection and command transmission and execution. The smart gateway connects to the router to synchronize data to the back end of the cloud platform. At the same time, users can connect to the cloud platform through the Mijia App on mobile phone to control the device and receive device information.
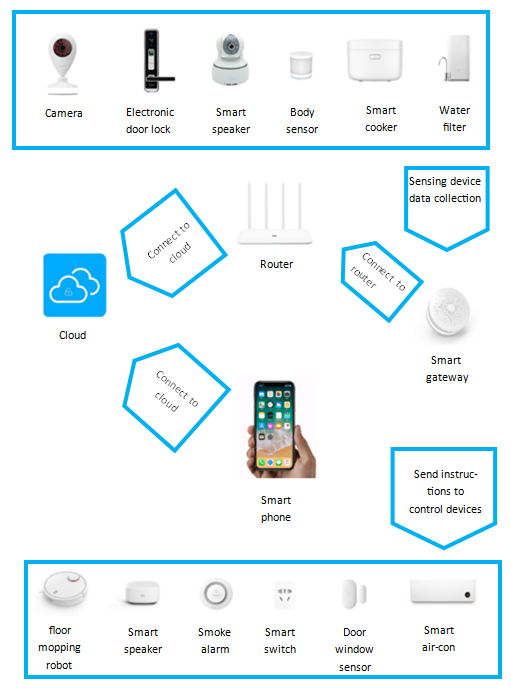
Figure 1: Mijia smart home solution
Through the research on the operation mode of Mijia smart home, the source of evidence is mainly divided into three parts, the mobile phone (back-end cloud), router equipment, smart gateway and sensor equipment connected to it. The three parts are briefly introduced below.
Through the mobile phone Mijia App, it can be synchronized to the cloud to operate the instructions of the sensor device and some events generated by the sensor. The mobile phone data is mainly stored in directory of the Android phone: /data/data/com.xiaomi.smarthome . This instance is an event generated when the Mijia human sensor detects a person passing by, and the event content and occurrence time .
The router records the information of a large number of devices connected to the network, and forensic extraction can be completed by synchronizing logs or imaging. As shown in Figure 3, the log file downloaded from the Xiaomi router records detailed information such as the mac address, name, and assigned IP of the device. Figure 4 is the result of the analysis of the image of the Xiaomi router extracted by the imaging tool. It contains log information of multiple messages, and the one with the gz suffix is the backup of the previous log.
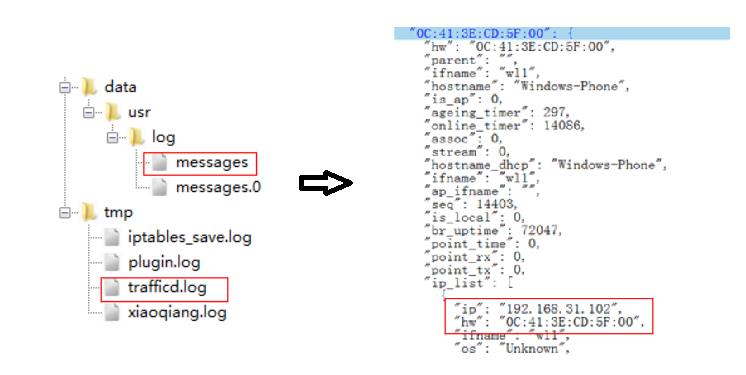
Figure 2: Xiaomi router’s log
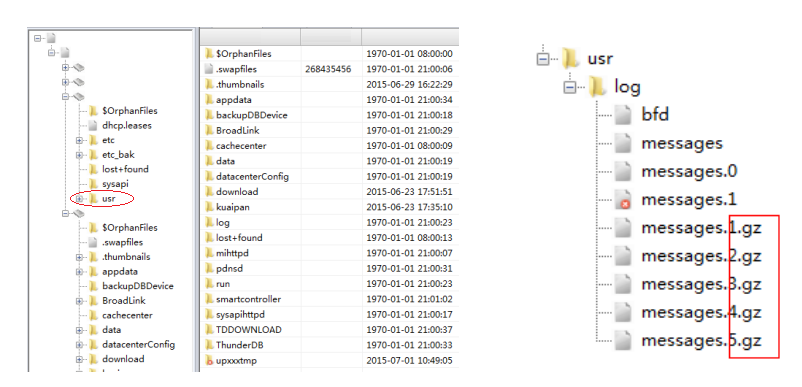
Figure 3: Image extraction from Mi router
The Mijia smart gateway uses the ZigBee IoT protocol and does not have a network port to connect for communication. It is very difficult to extract data through intrusion methods. Figure 5 is the disassembly diagram of the smart gateway. Through the disassembly of the chip, no general flash memory chip was found. The data is mainly in the JN5169 ZigBee module (integrated CPU processing function), which is difficult to obtain. Different gateway manufacturers may have different designs.

Figure 4: Disassembly of the smart gateway
As an important part of smart home equipment, the camera has two main methods for obtaining evidence. First, use tools such as Xshell to log in to the embedded linux operating system through protocols such as ssh\telnet\serial, export the device image, and obtain its log files for further evidence collection. Second, restore data by making images of the disassembled nandflash, TF card, SD card, hard disk, etc. Then we can do further evidence collection. As shown in Figure 6, the data exported from the Xiaomi camera is the jffs2 file system, and the red part in the figure is the IP address logged in to the camera.
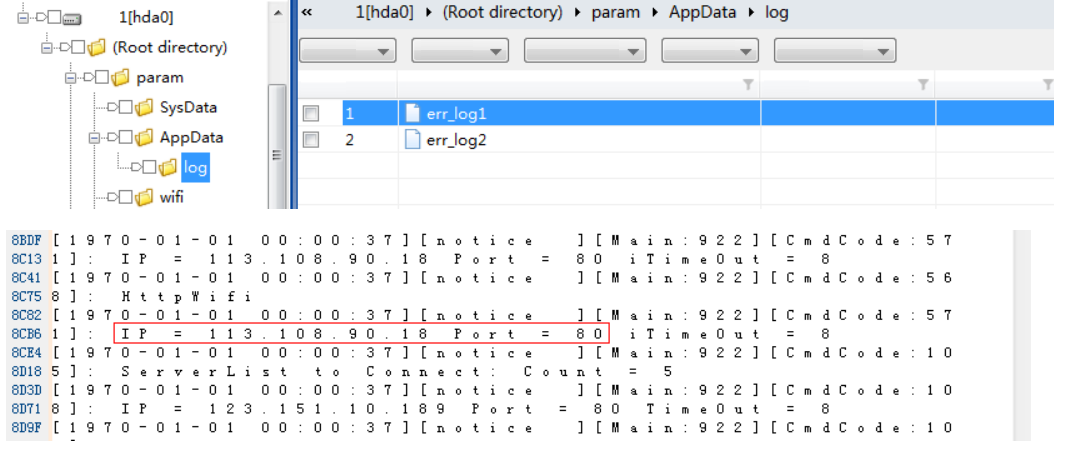
Figure 5: Camera image analysis